DATA BACKUP & PROTECTION
A solid backup setup not only protects against cyberattacks, but also ensures data loos prevention and recovery, in case the information is accidentally
deleted, the work device gets stolen, or the hard drive gets corrupted of fails.
For higher security and data backup we offer the possibility to host data in two additional data centers.
We run a daily backup of all our database servers (HANA and SQL). This backup is stored on a dedicated backup server in another network.
When we set up a cloud environment, our main focus is to secure all the data and build a solid data security structure for the organization.
Security consists of several important settings, such as how data is stored, accessed, saved and protected.
DATA STORAGE
We work with encrypted data volumes.
When data is encrypted, no unauthorized individual or entity can access and read it.
NETWORK & DATA STORE SEPARATION
Each customer has its own storage which is not connected to any other system or customer.
It is highly unlikely that someone can get access to the data center and remove any equipment.
The security features such as fingerprint readers, access cards and restricted access meet the highest standards.
DATA / ENVIRONMENT ACCESS
We ensure data access via an encrypted Site2Site and Dial In VPN connection free of charge.
The SSL-encrypted RDS connection is also available, making the system accessible through a web browser via HTML5.
For higher security, we also provide 2FA. This service works with Sophos mechanism and a software token system on your cell phone.
FIREWALL
We use state-of-the-art firewall and antivirus systems, therefore, Sophos is our partner of choice. IDS and IPS are implemented.
The configuration includes intrusion detection and standard port blocking.
BACKUP
All hosting offers come with an external backup solution, that copies our data to an independent and not permanently connected storage.
This protects the backup from being encrypted if you are hit by ransomware. The backup runs minimum once a day. If needed, we can also create an ongoing backup that mirrors all your data to an external storage.
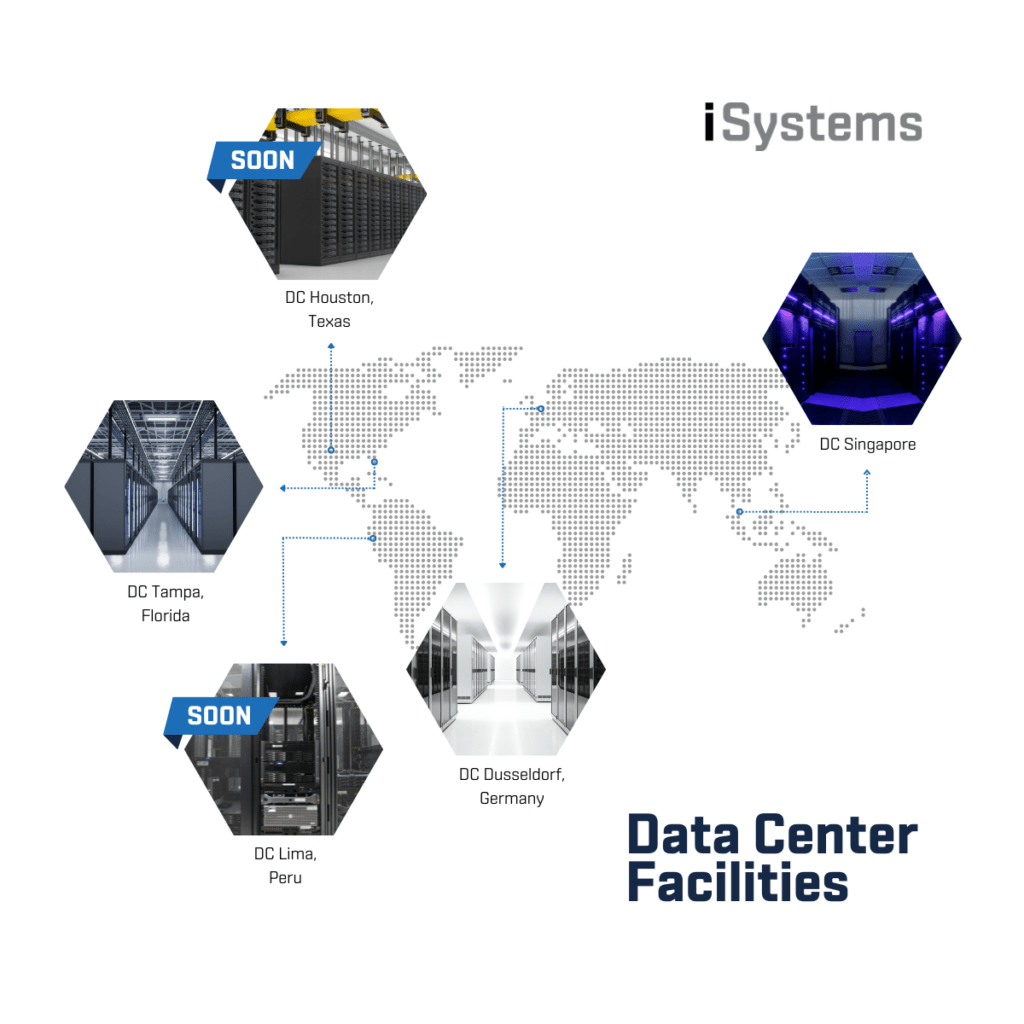
OUR DC FACILITIES
DC FACILITY SPECS
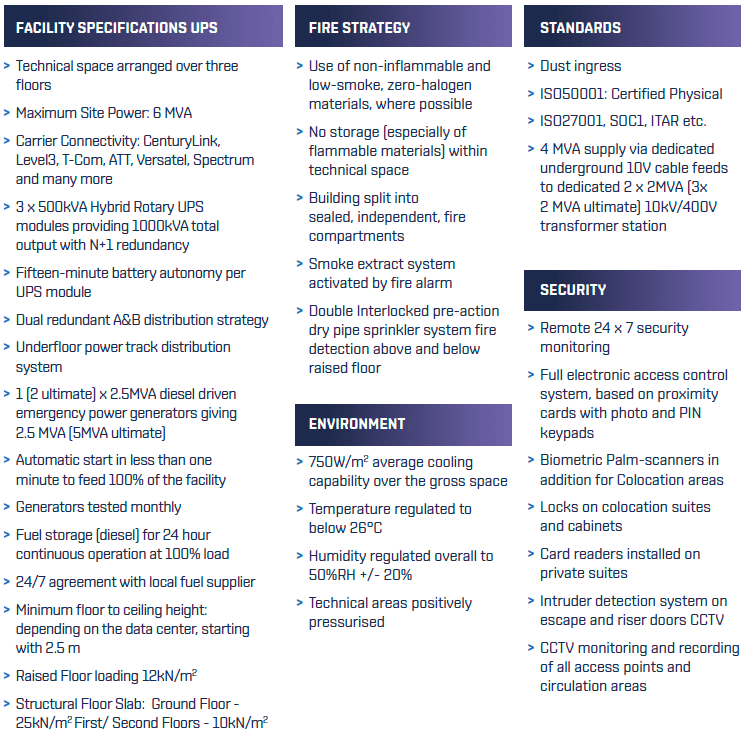
EXTENSIVE SECURITY
Besides our regular DC data backup protocols and security procedures (data storage, data access and Firewall), our experts recommend companies of
all sizes to also consider an external backup (additional off-site backup) – a local replication device that can assure a higher protection of data in the event of catastrophic failure and outrage, and Sophos cybersecurity (MDR) – 24/7 Threat Detection and Response service.
1. BACKUP OFF-SITE DEVICE
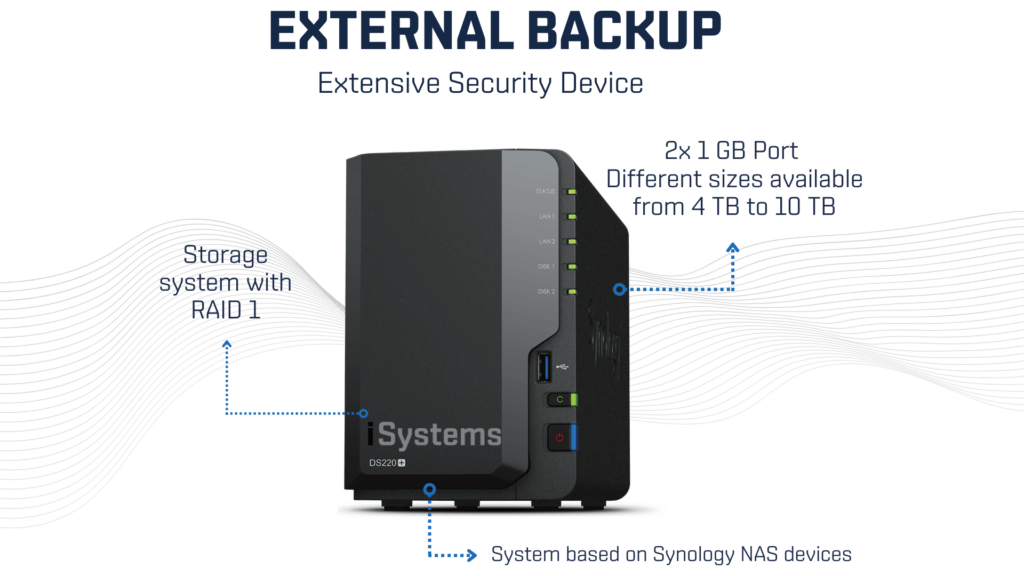
HOW IT WORKS
> Backup store on customer’s site
> The device only needs internet connection
> Any router or ISP connection with DHCP can be used
> The backup is transferred through a push pull system between the data center and a storage
> The storage is based on a sinology and equipped with a special connection tool that establishes a secured and encrypted tunnel between the storage and the backup server
> No firewall rules or any other configuration are needed
REQUERMENTS
> Internet Connection with minimum bandwidth
of 25 Mbit, 50 Mbit are recommended, 100 Mbit is optimal
> 1 GB Port on the router or switch. Wifi is NOT an option
> 110/220V power outlet with 2 Amps
Different plug types Nema, EU et care available
TECH SPECS
> Storage system with RAID 1
> 2x 1 GB Port
> Different sizes are available from 4 TB to 10 TB
> Retention policy starting at 10 day up to customers choice (depends on the device space size)
> System based on Synology NAS devices
2. CYBERSECURITY SERVICE
Sophos Managed Detection and Response (MDR) is a 24/7 managed threat protection, detection, and response service.
The MDR service tier provides analyst-led threat hunting, investigation, and threat containment so attacks are interrupted to prevent spreading.
Sophos Firewall is already included in our datacenter, also Intercept X and Server protection for all our data center services.
The customer may book Intercept X and Server Protection for their local network, managed by our experts as well.
THREAT HUNTING
> Proactive 24/7 hunting by our elite team of threat analvsts
> Determine the potential impact and context of threats to your business
INCIDENT RESPONSE
> Initiates actions to remotely disrupt, contain, and neutralize threats on your behalf
to stop even the most sophisticated threats
CONTINOUS IMPROVEMENT
> Get actionable advice for addressing the root cause of recurring incidents to stop them for occurring again
XDR-ENABLED
> Sophos XDR is included so Sophos analvsts can detect and neutralize security threats from all available data sources while you can identify and remediate IT issues across estate
We would love to hear from you and answer any questions you may have

